Regain Trust. Eliminate Socially Engineered Fraud.
Trustmi’s Behavioral AI defends against attacks that exploit human trust—like phishing and impersonations—by analyzing anomalies across emails, financial systems, and controls. It protects your people and your money, restoring trust where it matters most.
See for yourself, request a demo.



Trusted to Protect $200B from Socially Engineered Cyber Attacks By:
THE PROBLEM
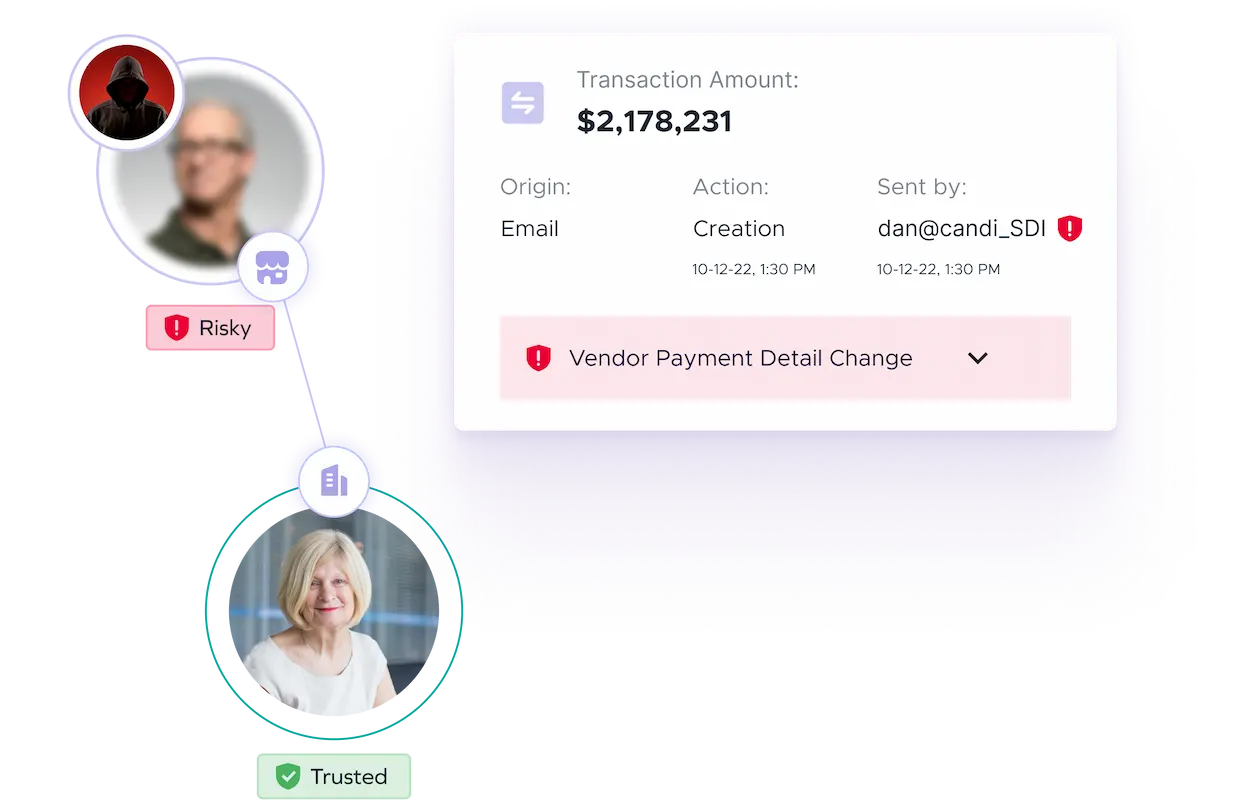
Socially Engineered Attacks Exploiting Trust to Commit Fraud
Financial fraud driven by socially engineered cyberattacks are a $100B+ a year problem that exploits human vulnerabilities, targeting vendor-facing roles including finance teams and executives who have access to funds. These attacks manipulate trusted individuals and processes, creating significant risks for businesses.
THE CHALLENGE
Increased attack sophistication paired with complex processes and siloed operations
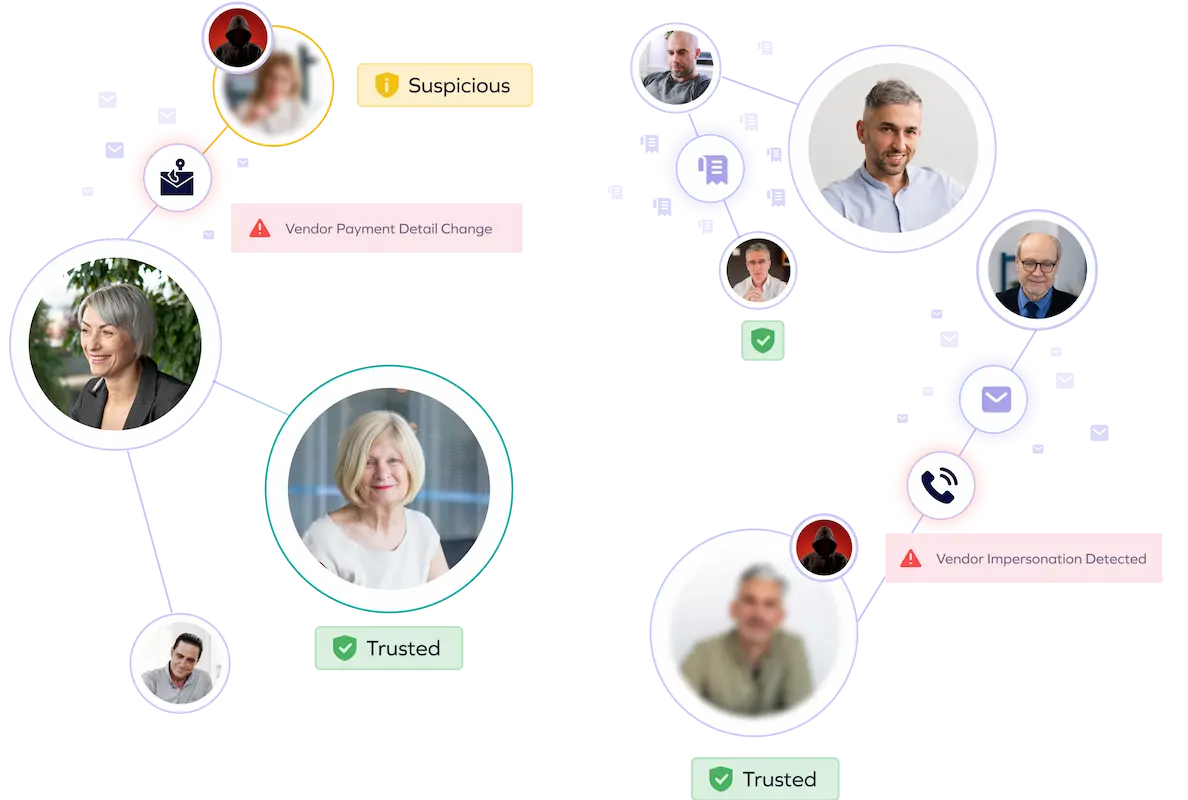
The rise of generative AI has fueled a surge in sophisticated socially engineered attacks—deepfakes, phishing, trusted app scams, and executive or vendor impersonations—that go far beyond email, infiltrating the entire payment ecosystem. Combined with massive, complex processes and siloed operations, businesses face a perfect storm of vulnerability.
OUR APPROACH
Trustmi’s Behavioral AI Platform Eliminates The Biggest Cyber Threat with End-to-End Protection
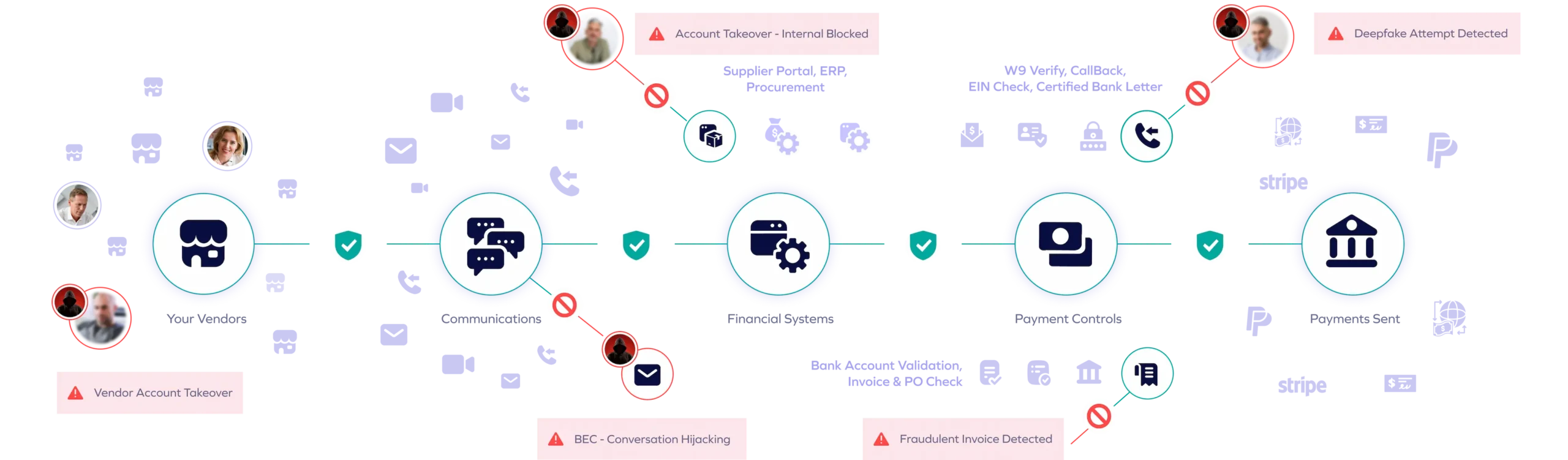
Trustmi delivers a centralized, fully automated solution that safeguards the entire B2B payment lifecycle, proactively addressing the root cause of financial fraud—socially engineered cyberattacks—while reducing manual effort and errors.
Trustmi pulls data from various financial systems and combines it with other critical data points to validate transactions in real time, stopping fraud attempts stemming from social engineering before they cause harm.
Trustmi analyzes patterns across vendors, payment data, emails, and financial documents, detecting sophisticated social engineering tactics and ensuring holistic fraud detection beyond limited channels.
Trustmi seamlessly integrates with your payment ecosystem, ensuring uninterrupted operations while delivering robust protection against socially engineered cyberattacks targeting your payments.
Trusted by Finance and Security Leaders






"Trustmi provided transparency into our payment process to see where cyberattacks and errors were happening and full protection without changing our workflow."
"Like many businesses today, we've experienced cyber attacks on our payment process, but we didn't realize the extent to which we were at risk until we evaluated Trustmi. Now we're confident we'll be able to avoid future attacks with their platform."
"Trustmi's platform is an important tool for our team. Their Payment Flows module increases our payment cycle security, and our team has also managed to cut down the time for preparing payments reports from half a day to half an hour."


